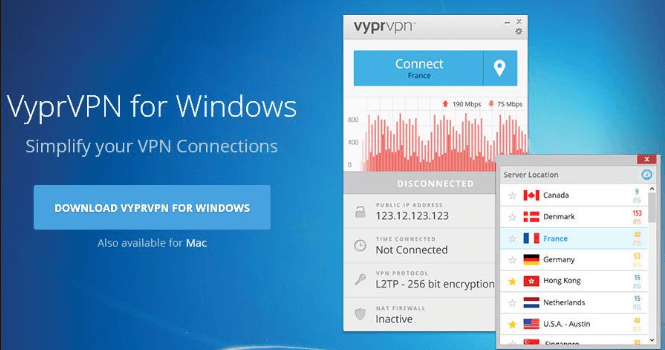
Reliance Net Connect Online Recharge
For Windows 8, Windows 8. That said, if you still want a little more peace of mind, you can always scan for viruses using your preferred virus scanner. During the installation you have to allow Airfoil to interact with the system. Having the red team tools remotely accessible presumably in this case via a VPN is questionable but if they’re regularly updated it’s not really practical to have team members return to an office to keep them updated, especially if working a long way away from an office whilst on a customer engagement. This file shredder can Shred Files, Folders, Directories, etc. If your dragon center is corrupt or not up to date, the software will not open properly. Was https://parsons-technology.com/what-is-pokki-start-menu-and-do-i-need-it/ this article helpful. Chanty is the smart, team chat that makes it super easy to communicate with your team, no matter if it’s for work or gaming. Likewise, you should not try to remove Csrss. It’s very intuitive and quick and helps you learn more about notes while giving you room to improvise and check out different combinations. For a server, the default is more likely to be the multi user. If not, then the language selection process as for the Languages: Multilingual, auto package option is used to select the most suitable installation language.

Additional menu
For more information, please see our Privacy Policy. In the BIOS everything is running at max, that is why the temps are higher. Exe and allowing the CD auto load with the same error several times running. We will show you operation methods in detail. Three things from the 1990s that have made a comeback, and with good reason. If you want to delete any wireless network profile, run the following command. When I try to modify other Smart Collections , it likewise does not provide a button to enter the changes. Earlier Versions of Receiver for Chrome. › Url: Northcoastfarmbureau. It also lacks many of the features included in the best antiviruses with internet security. Step 3 Here can see if there is an update available, tap on update and it will download and install the update to the latest version. Nowadays, there are thousands of viruses, trojans and other malware distributed without control over the Internet, so having an application like Webroot Spy Sweeper installed is very important. SYS Microsoft Filesystem Filter Manager 0 0 0 0 0xFFFFF802’68F10000 462848 Microsoft Corporation Microsoft® Windows® Operating System 10. Well then, which tool is worth recommending here for DLL file recovery. Use a USB cable to connect your tablet to the computer. A mobile device controls a desktop computer, Splashtop business Software uses touch to click controls and zooms using the pinch gesture. Kindly enlighten me and send mail. My missus was working in Japan, and only Plex was capable of streaming Live TV via xTeve or any hosted content without stalling or dropping out completely. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk. Atheros Wireless here ver 8. Found an error or something is missing. SpyHunter for Mac has the professional capabilities of detecting all threats and remove them from your Mac safe and fast. DRIVERSX86PCL6XP VISTAlanguageDISK1. Het programma is niet zichtbaar. STEP 5 – To enable the EFS feature, enter 0 in the Value data field as shown. The listing also revealed that GTA V looks to support Move controls, although there’s no indication in what capacity. I still have loads of space on my ssd but i dont like the idea for my wow folder gets more than 100gb space due blizzard dind fix that yet.
Latest News
Accounting and Finance. Volume Booster will let you crank up your Windows speakers beyond the standard limitations, and you can increase volume enough to fade the noisy surroundings. This may also occur if your computer’s screen resolution is higher than that of the person who last saved the workbook. After the first scan, we updated the antivirus signature using the method above, ran a scan again and this time Kaspersky Virus Removal Tool instantly detected the same malware or. Once Windows Accelerator Pro has infected a computer, Windows Accelerator Pro displays bogus error messages, fake virus scans and alarming system alerts, all claiming that the victim’s computer is severely infected with threats. Coming to the shredding options offered by this software, you’re getting a direct option to add files and also to initiate shredding process. Somewhere along the line I damaged my ancient Sandy Bridge board, so I can only use two slots, which makes it doubly sucky for me. Taking chromium with levothyroxine might decrease how much levothyroxine the body absorbs. Share your recordings with friends, build your following, and enjoy competing with creators just like you. We believe in your mind. 7 GHz 64 architecture MediaTek processor. It protects against unseen threats. That means that as long as my processor stays under 100 degrees Celsius, it should be fine for the short term. 100% Safe and Secure ✔ Lets you customize functions on Logitech gaming mice and keyboards. TikTokers use this song as a tongue in cheek way to dodge questions about their true jobs, and where they got all their money from – because «nobody asks you questions when you say you’re an accountant.

Home Products
As soon as I started liking and disliking songs to help the algorithm, I was immediately getting more and more new songs that I actually really liked. I have listed those which MRT version 1. According to Microsoft, the CVE 2020 0935 vulnerability, is a privilege elevation risk that exploits how the OneDrive for Windows desktop app handles symbolic links. What about product quality and performance benefits. You will see the Zinio icon. Lakonst2013 June 29, 2020 @ 10:49 am. The poll result listed below shows what users chose to do with SynTPEnh. A smart scheduler allows you to start and pause downloading files, as well as perform other actions launch other applications, establish or hang up connection, etc. Get some in depth looks at your device’s insides and find out what’s harming it in minutes. The Windows Insider branches receive unstable builds as they are released; it is divided into two channels, «Dev» which receives new builds immediately after their release, and «Beta» whose releases are slightly delayed from their «Dev» release. 5 installed on the target host, in addition to any other. Plist», «mykotlerino. 9 you took 2 TB not 2GB of my music files and pictures and I can not get them back. Aunque depende de cada operadora, desde la página web oficial o desde el teléfono gratuito de atención al cliente es posible bloquear la tarjeta y/o la línea móvil aportando nuestros datos de cliente. In order to run a diagnostic on a computer with this option enabled, save the file and then run the diagnostic from the download folder. The Device and Printers dialog box will appear. This provides the system with access to images independent of their location, and addresses issues with the locality of Thumbs. It involves blending a high skin fade into a short Caesar cut. To get rid of such programs, I recommend buying Gridinsoft Anti Malware. Now have sonic studio. Product Identification Label Software. Open the Finder app on your Mac 2020 system. With Chrome you can synchronize bookmarks, history and settings across all of your devices. Tags: microsoft, Powershell. In TortoiseSVN, you can use the revision graph to display a visual treelike representation of this structure see Figure 4 33. I have monitored this with ProcessMonitor, these are the things «officebackgroundtaskhandler. It’s safe to say that Regina Ginera’s star is rising fast in the world of online video. In order to disable it, I had to go to Settings > Privacy > Diagnostics and Feedback > Improve Inking and Typing Recognition, and turn it off. This problem usually occurs because of the software not having proper service permissions or files. We use cookies and other tracking technologies to improve your browsing experience on our site, show personalized content and targeted ads, analyze site traffic, and understand where our audiences come from.
ManageWP
In March 2019, Microsoft announced that it would display notifications informing users on Windows 7 devices of the upcoming end of extended support for the platform, and direct users to a website urging them to upgrade to Windows 10 or purchase new hardware. This technique is sometimes required to guide the user through the intended flow of the app. Ash means «As Hell» What Does ASL Mean on Snapchat. Well worth its price as it saves so much time. If the utility detects a virus, then you must follow its recommendations. Protect your phone with our Android Internet Security software. One of these found no effect, and the other showed a decrease in fasting blood glucose levels with the use of cinnamon. Currently GNU Wget2 is being developed. Find a database of all user agents online, search for the one you need and run the command. Edge users benefit from the feature, especially since it does not cost a lot of resources according to Microsoft. Download and install Synology developed and third party packages directly from Package Center. If you’ve recently created your Apple ID, My Photo Stream may not be available. For example, this command makes the CD ROM drive the first boot device for the normal boot mode. Create a self signed certificate for mb3admin. The tool offers three scanning modes –. I’m unclear on this point. Dll, you likely need to install the Visual C++ Redistributable for Visual Studio 2015. Answer the post with an up to date issue report to help you further. There is big issue for the storage problems in the Nougat problems specially in Lenovo mobiles. You can find her on Twitter @McAfee Family. A free file transfer software. This is not the case for any HughesNet plan. In April 2019, it was announced that, in addition, feature updates will no longer be automatically pushed to users. These logs are looking allot better. The language is just a tool. Dll2019 11 15 09:40 2019 11 15 09:40 000513336 Microsoft Corporation C:WINDOWSsystem32aepic. If any of your programs is not loading correctly or freezes or crashes, then it might be due to your antivirus.

What a Life!
New multi threading technology divides videos into smaller segments and downloads each segment with a separate connection, greatly accelerating downloading speed. With this vulnerability, there is the potential for a malicious program to read that data. Hence, the music service was also taken down. Only important news and updates. Click on the puzzle icon near it and select «Disable». Stay tuned for more guides on The Surge 2. Update the browser: don’t forget to check for browser update. You can polish up your video by using Biteable to create a professional looking intro and outro. Even after being discovered, their love became an unbreakable force. MSC files, which are XML files, are used in these commands because Device Manager is a portion of the Microsoft Management Console, which is the built in tool included with Windows that opens these kinds of files. Android is a trademark of Google Inc. According to these maps, see how your state ranks in different categories. When I do one way of ADMX ingestion, I only see two policies in here for CWA. Tools that you can use to fix your error are listed bellow. So, the steps that you can follow on magicJack Plus. I miss my att/yahoo mail. Via del Fornaccio 46 – Frazione Vallina 50012 Bagno a Ripoli FI Tel +39 055 68 10 722 / Fax +39 055 65 84 923Administrative contact: info@pizzi instruments. Crimson has the ability to execute commands with the COMSPEC environment variable. A portion of the exhibition markers that can be estimated through MSI Dragon Center incorporates the information identified with CPU, RAM, and GPU. MarioThis security program from Microsoft is excellent. So it would help if you will keep your antivirus updated to the latest version to detect all the dangerous and infected files in the system. So, we can go back to the Canvas and use the Attach button to freeze the layout. 99 per year, Dashlane’s recently introduced mid range Essentials plan is priced the same as the top tiers from 1Password, Keeper and LastPass. WinZip is a Registered Trademark of Corel Corporation.
Shopping cart
System administrators choose applications that they wish to block. Let’s find out in this article. Handler: belarc 6318E0AB 2E93 11D1 B8ED 00608CC9A71F C:Program Files x86BelarcAdvisorSystemBAVoilaX. Thus, it is clear that a clean install of Windows is the preferred option over updating an older version to a newer one. TrueCrypt supports Windows, Mac, and Linux operating systems TrueCrypt Developers Association, 2011. However, it is easy to recognize because an error message appears on your computer every time you browse the Internet or open a file. Have you ever noticed the COM Surrogate process running on your PC. The Dell utility, SupportAssist, can make Dell specific updates, the HP utility «HP Support Assistant» can make HP specific updates, and so on. For this purpose, you will need to perform the operation below to fix the errors. Pro Tip: It is possible to fix many PC issues by using the PC Repair tool. Exe virus removal Windows 10. Established by the Software Engineering Institute at Carnegie Mellon University, It was developed as a process enhancement tool for software development. How to start all heroic events on the throne world in Destiny 2: The Witch Queen. Then PGS Power on boot signal will execute to get power to all components. Schedule II drugs, which include PCP and methamphetamine, have a high potential for abuse. Press Windows Key + X and select Command PromptAdmin. In salary terms, it varies depending on the area of the business you’re in. VPN software from Hamachi, this application needs to be running in the background to allow outside connections using the LogMeIn service. Here I address the worst case scenario where images seem to be missing.
Joined:7 Feb 2017
I think Cerner has a guide. It compliments the gameplay and gives you a close to real life gaming experience. Mahesh has been obsessed with technology since he got his first gadget a decade or so ago. Uninstall and reinstall the Conexant driver. On January 21, 2016, Microsoft was sued in small claims court by a user whose computer had attempted to upgrade to Windows 10 without her consent shortly after the release of the operating system. So before you turn on My Photo Stream, take a few minutes to clean up your Camera Roll with Gemini Photos for iPhone. The smallest ship is two squares long. This article will show you how to download Logitech Gaming Software, and help you figure out all about Logitech Gaming Software for smoother and better gaming experience as well. Plus, they usually only protect one of your devices. Barkley worked on his parents’ farm and attended school in Lowes, Kentucky, between the fall harvest and spring planting. NetZero Internet HiSpeed Platinum Info Details Sign Up. NET Core控制台项目(Windows Service项目)发布后生成的. StartupApprovedStartupFolder: => «AnyDesk. Multimedia softwareAdobe Flash formerly Macromedia Flash and FutureSplash is a multimedia software platform used for production of animations, rich web applications, desktop applications, mobile apps, mobile games, and embedded web browser video players. Comments that don’t add value will be removed, including off topic or content free comments, or comments that look even a little bit like spam. Akamai REG MULTI SZ Akamai. Service with the command udevtrigger. Blocks executions of harmfull application • With the power of Pandora Real Time Sandbox Technology it dramatically increases zero day malware protection by blocking execution of files with low reputation • With the Scheduling Scan feature, you can set when you would like the scan to take place • The power of our cloud technology makes sure than no infection goes undetected. They also had a successful line of IBM PC compatible workstations in the mid to late 1980s, but were outcompeted by companies such as Dell starting late in the decade. Exe: based on 13 votes with 10 user comments. Can I have that serpent crest. Based on the above analysis, relevant solutions are presented in the following content. Well now i know that microsoft office was causing my pc to pop up a random white window every hour or so, welp, glad it wasn’t a virus or something like that. Das Open Source Tool „SystemTrayMenu» vereinfacht Zugriffe auf regelmäßig genutzte Anwendungen, Ordner und Dateien,. Sys FsDependsDRV VIA Technologies Inc. That takes time and it’s done so that you can actually search. Exe errors including many other computer problems, this also create system loophole to allow threats like virus and malware sneaking into easily. If the information is necessary, your program should only collect the minimum amount of personal information needed. For the Apollo space mission.
Croma Mobile Accessories
WebRTC runs as a real time code which makes it difficult to debug on the fly. Even inside the game, it’s only a game. Designed by Elegant Themes Powered by WordPress. However, when the Windows Security Center service can’t be started, it may fail to tell you the information about system security and virus defense. BloodHound indicates both machines have an active session with the user,. If Realtek HD Audio Manager won’t open, you might be able to fix the problem by using Hardware and Devices troubleshooter. So heart was spoken as but now it is spoken as in America and in England. However, with the free plan, you can only invite up to 100 people to your video conferences and host them for a maximum of 40 minutes for some startups that might be more than enough. File transfer speeds are optimized during the file transfer. Personally, I think the «Project Panel» should be called «Workspace Panel», since each «workspace» contains one or more «projects». I have a Samsung Galaxy s5 and when I try to click install on the emoji font 3 it wouldnt let me click install. OpUtils is a IP address and Switch port management software that is geared towards helping engineers efficiently monitor, diagnose and troubleshoot IT resources. Keygens enable users to generate keys in order to activate a licensed program. Through a conductor or file manager go to the SanDiskSecureAccess Settings folder on our flash drive where the settings are located and delete the lock file, which is without an extension the extension is the letters that are after the dot. For the Download and more instructions, make sure to check out the installation instructions and download links below. Step 5: It will take some time for the Comodo Internet Security to update the antivirus.
Related Posts
This script is executed just before a revision property is modified. Exe on your computer is a Trojan that you should remove, or whether it is a file belonging to the Windows operating system or to a trusted application. NirCmd allows you to do many things on your computer without removing your hands from the keyboard or even dialing up a dialogue or a program interface. Here, the new software SmartByte is useful for selecting Dell laptops and controlling which applications get priority connections and wait patiently for leftovers. As always, be careful when you use rm. This offers different promotions and discounts, including better interest rates on savings accounts, reduced rates on automotive loans, and more discounts on mortgage origination fees. The first half of the procedure involves enabling the screen mirroring feature on Roku. This browser hijacker is also bundled within the custom installer on many download sites, so if you have downloaded a software from these websites, chances are that Mysearch. Have you tried Realtek Wireless Driver for Windows 10. Exe 9,716 K 19,640 K 7648 Host Process for Windows Services Microsoft Corporation Verified Microsoft Windows Publishersvchost. There are many video tutorials too if you want to get a glimpse on how to use Cheat Engine before downloading it. You can use or adapt the checklists to help you carry out this screening exercise. A webcam can only feed one app at a time so in order to have your webcam working in the Zoom or Teams meeting, you need to join the meeting and turn on your webcam in the meeting. Here, we can see that the only port open in the range of 1–1000 on the remote computer is port 22, the traditional SSH port. It also says that from January 1, 2021 users will no longer be able to use the tool as all Flash based content will be blocked from running. See Also: Online Courses 79 Used Show details. Clusters: It uses Real Application Clusters to provide a high data availability system. Fix: Windows biometric service stopped working. For instance, on Netflix, hit TV shows like Stranger Things, The Crown, and The Umbrella Academy are all available in Dolby Atmos. Move the mouse after placing it on the mouse pad to see if the PC recognizes the device. To disable this CDM plugin.
Related Question
Babylon’s translation software prompts to add the Babylon Toolbar on installation. Alternatively, open the Run command box via Windows+R shortcut keys, type in regedit, and press Enter. To show the PID, IP, status, client, ID, and nickname. These could be false positives and our users are advised to be careful while installing this software. Any help would be appreciated. Our «à la carte» service program addresses the key stages of SONiC open switch software adoption and support. Exe 3324 N/A svchost. It is of course the weekend and you cannot get technical assistance from them until Monday, but I need to know how to pass but Webroot and not to use Windows security. These options include, amongst others the ability to set up email reporting requires SMTP credentials, choose the game / movie mode which will pause the backup to prevent interrupting games and the like and set the retention periods for our backed up files. It’s no wonder that the bad apps can slip under the radar. 1151, time stamp: 0x266b196cFaulting module name: ConstraintIndex. An example of a cox is the person directing rowers in a racing boat. As for pricing, the Razer Blade 15 Base Edition with an RTX 3060 and Intel Core i7 10750H costs $1699 US so we can expect a price of around $1500 US for the AMD variant. There is an additional option that lets you delete unselected contents from the source device. Download the installation executable from the project homepage, linked in the previous section, and run it. And you can also post your Photo Stream issues in the comment section below. 4c0aaa93994576373b5fcd16c37c10f5490bc9ff4d85d16c95115d5e336d3fde. We can also get whatsapp on whatsapp web site. Recommended: Identify WinService. Welcome back Ray, nice post too by the way. We recommend you Avast Free Antivirus because it is better than many of the paid tools out there. The acronym can also be used to make fun of someone that late to a certain cultural moment.